The process of RFID access control and its Specification
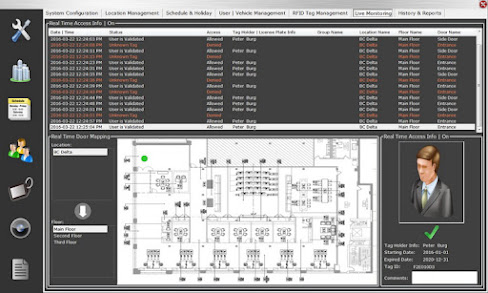
A standard RFID-based high security system includes 1) tags with unique identifying data capable of allowing or refusing entry to secured areas, and 2) a method for scanning the RFID tags at access command posts. RFID access control can be attached to items or incorporated in cardboard or plastic ID cards. They can even be lodged beneath human skin, however this is heavily debated. When the tags are read at access command posts, their data is confirmed against a database in a centralised surveillance system, and access is given or refused. The centralized security system can not only regulate access using identifying details, but it can also be connected with other services as part of a holistic security solution. For example, an RFID security system may be programmed to automatically track the number of users and hackers per ID and to activate surveillance cameras when a certain threshold is met. When a person attempts to enter an area where he or she does not have authority, the sys