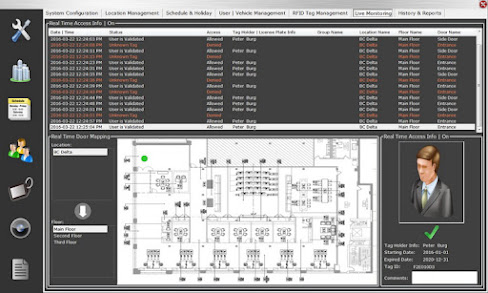
The process of RFID access control and its Specification
A standard RFID-based high security system includes 1) tags with unique identifying data capable of allowing or refusing entry to secured areas, and 2) a method for scanning the RFID tags at access command posts. RFID access control can be attached to items or incorporated in cardboard or plastic ID cards. They can even be lodged beneath human skin, however this is heavily debated. When the tags are read at access command posts, their data is confirmed against a database in a centralised surveillance system, and access is given or refused.
When a person attempts to
enter an area where he or she does not have authority, the system identifies
this and can activate video surveillance as well as transmit notifications to
protection or other authoritative officials. Even if a person has clearance to
enter the security perimeter, video recordings can be started to monitoring the
person's behavior while within.
Regulating building access with Long range
rfid reader [A1] has a few drawbacks that
should be addressed before deploying such a system. The first is that if an unauthorized
individual "tailgates" an authorized person through an access point,
the mechanism can be evaded. It should be highlighted, nonetheless, that this
is additionally a drawback of the previously described conventional access
control methods. A second problem is that the system may be thwarted: RFID tags
can be copied using inexpensive technology. Someone with an RFID reader may
"skim" information from an identification tag and create a new ID
badge with the required access rights.
For More Information :- https://www.nephsystem.com



Comments
Post a Comment